You have around 15 minutes to safeguard your content and act to take down a live stream. As piracy becomes steadily more reliant on live streaming, why real-time watermarking is a genuine game-changer.
The figures associated with video piracy are alarming, but too often they are so big that it is difficult to really understand them. So, let’s start small and one story from July in Broadband News that highlights how content piracy has become a lucrative business for those involved in it.
Italian police cracking down on an individual Sky Italia pirate, Zsat, tracked down a 35-year old man in Palmero. They discovered €186,000 in cash and two ‘wallets’ stuffed full of crypto-currency in his bedroom, while a banknote counter and gold bars were found hidden in a toilet and garbage disposal areas. The flat also contained 57 Sky Italia decoders connected to equipment for retransmission over the Internet and to what is estimated to be Zsat’s 11,000 customers across Italy.
It’s an impressive enough haul from a single rogue operator, but it’s also a drop in the ocean. So let’s start to widen the picture. Italian police estimate that video piracy is a €700 million yearly business in Italy alone. And when you start to look at it on the global scale those millions turn into billions. A recent Parks Associates report 360 Deep Dive: Account Sharing and Digital Piracy estimates that video piracy this year will cost Pay-TV and OTT providers $9.1 billion in lost revenue. That number will swell to $12.5 billion by 2024, representing a 38% growth rate. Parks also reckons that 27% of US broadband households currently engage in some form of piracy or account sharing (a subject we have examined before in What’s mine is yours: The problem of password sharing).
The importance of a top-down approach
The problem is that content, whether live or VOD, can be pirated at any point in its life cycle. Once the image is captured then it is under threat. Piracy can occur at any point in the production workflow: on set, in post production, at screenings, during distribution, and, of course, at the point of consumption. What we therefore need to consider is a top-down approach to combating it. This is where watermarking comes in. Unlike many other approaches it travels with the content all the way along the chain.
And it needs too. Whatever the security level inside a STB, there are easy ways to access the stream by spending a few dollars on some specific (but easily available) AV components and deploying them with some basic technical skills. While piracy can be very sophisticated indeed, at its base level its not rocket science. Couple that with the increased penetration of high speed broadband and the ease with which users can find illicit content, and you have the perfect condition for a boom as the graph below shows.
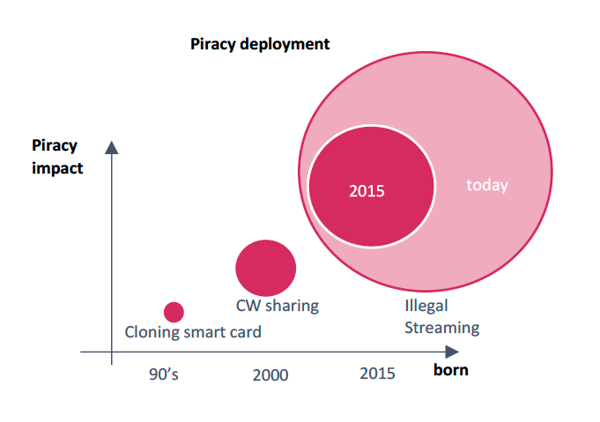
Watermarking can end that boom but it needs to be considered as part of a system not as a solution on its own. Placing a watermark in a video stream is worthless if then you do not have robust additional security products required to first detect it and then to take action.
It is an elegant workflow when done properly.
- The content is marked at device level
- The web is crawled in search of illegal content distribution
- The mark is extracted and the source of the leak identified
- Progressive measures are escalated to stop the stream. These can start from a simple online notification and scale to visits from law enforcement
One other advantage of a top-down approach; it can also be utilised at any point in the chain. This makes watermarking suitable for content owners such as movie studios and sporting leagues, as well as distributors and operators.
The Drive Towards Real-time Watermarking
One thing that it is very important to note is that the movement towards watermarking is not a new one. Yes, watermarking has existed in the video industry for decades. Many viewers will be familiar with the client-side watermarking technology that composits a graphical overlay over the video stream in the client device and provides a numeric identifier for what device is screening the content. In case of a breach this can be easily identified. However, this can be as easily identified by a pirate operation and removed, so the sophistication of client-side watermarking is ramping up and the industry is moving on.
What it’s moving to is a dynamic solution. Legacy watermarking is static. It is not a technology that iterates quickly and, with the increased sophistication of modern video piracy, it needs to. The pirates iterate very fast, and so the effort put into trying to prevent breaches must as well.
It is very much a game of cat and mouse with innovation on both sides. Anyone who has closely followed the actions of a top pirate set-up will end up with a grudging admiration of the skills involved, as well as an equal determination to negate them. That means that companies such as ours developing a watermarking solution need to be agile and swift to adapt to emerging pirate competencies; leaning on decades of experience and knowledge to always keep one step ahead.
Dynamic does not just mean realtime, though of course this is a key component of the whole battle against illegal streaming; a solution needs to have the tools that can ensure the takedown of content when an event is happening not some time in the future. In our interview with Gaëtan Le Guelvouit, from our industry partner b<>com who we are developing a solution with, he mentions a 15 minute time window. But in the context of watermarking, dynamic also has to mean agile evolution and a software-based solution that can be constantly updated to keep ahead of the multi-million Euro industry it is trying to suppress.
An effective watermarking solution also needs to be fully-deployable and include legacy devices, robust in that its watermarks should stay with content all the way through the chain and even be retained and detectable even after a breach; fast and detectable in seconds to allow all the other parts of the suppression efforts to take place in that crucial 15 minute window; imperceptible to viewer and pirates alike; low latency; and scalable up to millions of devices with no impact on speed.
As Le Guelvouit points out, developing piracy solutions need to follow the NIST framework of Identify, Protect, Detect, Respond, and Recover and this is exactly the approach we have taken to our Anti-Piracy Center. And with demonstrations taking place at IBC and field trials starting after the show, this is exactly the approach we are taking with dynamic watermarking too.
Meet with us at IBC on Stand 1.A51 to find out more!


