This Cybersecurity Awareness Month, it's worth remembering that while TV industry discussion about cybercrimes usually relates to video piracy, the increasing sophistication of ransomware attacks shows that is not where the danger ends.
 Ransomware does exactly what it says on the tin. Once downloaded and a machine is infected, it boots up and locks and encrypts a victim’s computer data; the criminals then send a ransom demand to restore access.
Ransomware does exactly what it says on the tin. Once downloaded and a machine is infected, it boots up and locks and encrypts a victim’s computer data; the criminals then send a ransom demand to restore access.
It’s a crude tactic but an effective one, and it is worth pointing out that some of the software and techniques involved are anything but crude and are very sophisticated indeed. Recent years have even seen a rise in so-called Ransomware as a Service (RaaS) models, where threat actors develop new malicious software and, rather than go through the whole process of launching attacks themselves, sell access to it to others. This allows affiliates to launch their own ransomware attacks, widening the scale of the threat.
According to Statista data, the number of organizations affected by ransomware attacks has grown steadily from 55.1% in 2018 to 72.7% in 2023. If that wasn't concerning enough, the economic impacts have grown much faster since 2017 when the WannaCry crypto worm - still the single most devastating attack yet, which infected around 300,000 computers - disrupted multiple companies in multiple sectors worldwide.
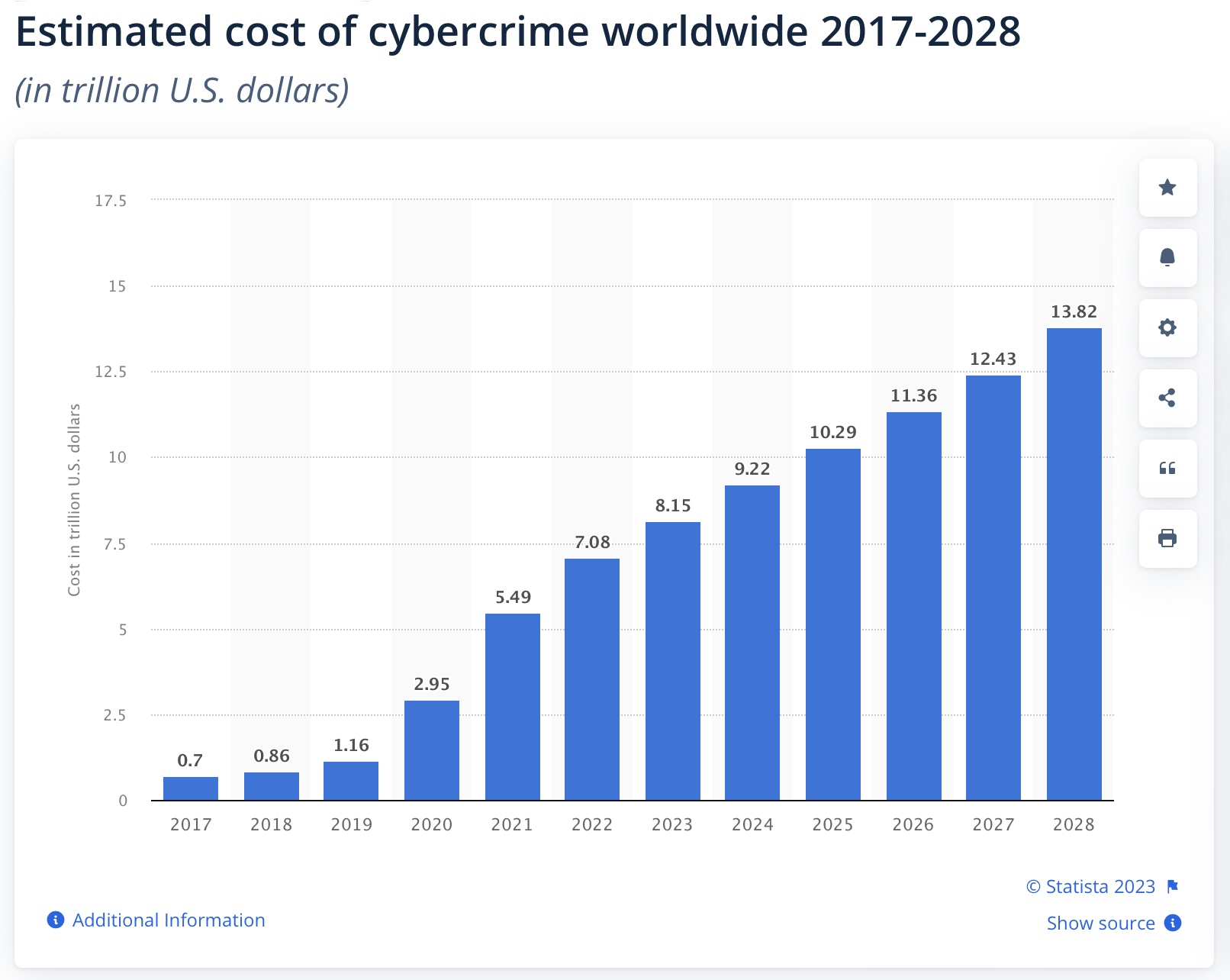
The following graph shows the impact of cybercrime from 2017 up to 2028. And it is worth remembering that in 2022, approximately 68% of the worldwide reported cyberattacks were ransomware.
Nearly 155 million ransomware attacks were detected worldwide in Q4 2022.
"In the second quarter of 2023, 34 percent of ransomware attacks in worldwide organizations resulted in a ransom payment, down from 45 percent in the previous quarter," Statista details. "Despite this, the average amount of ransom paid increased more than twice during the same period, going from nearly 328 thousand U.S. dollars in the first quarter of 2023 to over 740 thousand U.S. dollars in the second quarter of 2023."
The media industry is in the crosshairs. Three stations owned by the Cox Media Group in the US were taken out in an apparent attack in 2021 (as NBC News put it referencing other high-profile attacks that year: “First it was gas. Then it was meat. Now it’s local television stations.”); Sinclair Broadcast was targeted the same year; the UK's Guardian Media Group was hit in December 2022; and there are likely many more that fly under the radar...
The 5 main types of ransomware
There are five main types of ransomware:
- Crypto-malware: Encrypts the user’s files and demands ransom, often removing backups. Sophisticated crypto-malware uses advanced encryption, so files cannot be decrypted without a unique key.
- Lockers: Infects the operating system, especially on mobiles, and completely locks the user out, denying access to files or applications until the ransom is paid.
- Doxware (leakware): Derived from ‘docx’ hijacks the computer and threatens to publish the user’s stolen information online if they don’t pay the ransom.
- Scareware: Fake software that acts like an antivirus or a cleaning tool but locks the computer or sends numerous irritating alerts and pop-ups. It claims to have found issues on the user’s computer and sends deceptive pop-ups to purchase scareware, repair alleged errors, or demand money to resolve the issues.
- RaaS (Ransomware as a Service): As already mentioned, the relatively new kid on the block is malware hosted anonymously by a hacker. These criminals for hire distribute the ransomware and collect payments to manage the decryptors (the software that restores data access) in exchange for their ransom share. This means that whereas previously, those demanding ransom were skilled hackers, even non-expert coders can now exploit this field.
The first draft of this post dates back to 2021, and we've kept the following two paragraphs in to show how the jeopardy has increased dramatically in the time since. Compare the average ransom demand here to the one given above: the increase is 380%.
According to ransomware experts Coveware, the average ransom demand was $154,108 in Q4 of 2020. There are two main pressures on this value. On the one hand, fewer companies seem to be giving in to the demands thanks to effective counter-measures including, but not limited to, robust back-ups (see below). On the other, there has been a meta-trend recently for more extensive and larger companies to be targeted, the hackers realizing that their efforts can scale to corporations as easily as small to medium businesses, with the potential rewards increasing in line with company size.
“The biggest change over the past six quarters is threat actors now realize that their tactics scale to much larger enterprises without much of an increase in their own operating costs. The profit margins are extremely high, and the risk is low,” writes the company.
How to prevent ransomware attacks
So, whether you are a large broadcaster or start-up operator, how can you protect yourself against ransomware attacks?
First, backup. Backups are the single most effective tactic against ransomware attacks. If your information is backed up, ransomware is ineffective, and you cannot be held hostage. Ensure that they are stored offline and can quickly and safely be reinstalled. In addition, consider an additional backup in the cloud.
Netflix, by way of example, has been evangelical in insisting on a 3-2-1 backup rule with all its suppliers — keep at least three copies of your data and store two backup copies on different storage media, with one of them located offsite — and the industry is tending to adopt it as best practice.
Elsewhere, consider adopting two-factor authentication (2FA) or multi-factor authentication wherever possible, strategies that can be further strengthened via biometric data. It’s also worth looking at Dynamic Control Access, which segregates your network into distinct zones requiring different credentials. This ensures that a single attack cannot compromise your entire network.
Unfortunately, your weakest point is often not your network but the people that use it. Conducting regular employee security awareness training can help with this, as can installing anti-malware / ransomware software and running frequently scheduled security scans alongside automating software updates and patches. Purchasing ransomware insurance is also a sound move, though premiums are rising. This is partly driven by the fact that bad actors were, unfortunately, swift to realize that they could use generative AI to scale the likes of phishing attacks dramatically.
All these measures may not completely prevent a ransomware attack, but they can significantly reduce risk and mitigate the damage should an attack occur.
Original article: Esther Levine

